Server configuration
Server Configuration
In this section we will cover:
Logging In
Creating a new user
Disable root login
Disable password login
Logging in
When you provision a new server, you will be provided a username, password, and ip address. Generally that username will be root. Let’s log in with them now in the form of ssh username@ip .
Initiate login to server
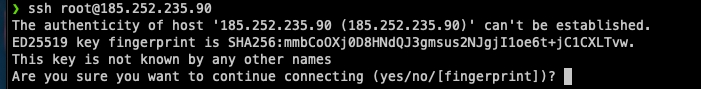 SSH into the server
SSH into the server
2. Type Yes
3. Enter password
 Logged into root
Logged into root
You are now logged into root. However, we do NOT want this as an option, so let’s fix it.
Create New User
Since we no longer want to be able to log in as root, we’ll first need to create a new user to log into.
Create a new user
You’re going to want to choose a unique username here, as the more unique, the harder it’ll be for a bad actor to guess. We’re going to use mellamo .
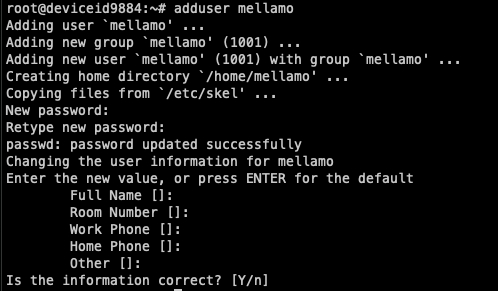 Create user mellamo
Create user mellamo
You will then be prompted to create a password and fill in information. Don’t worry about the information, but make sure your password is complicated!
2. Give them sudo privileges
sudo is the name for “master” privileges, so we need to modify the user to add them to that group.
3. Verify user has sudo access
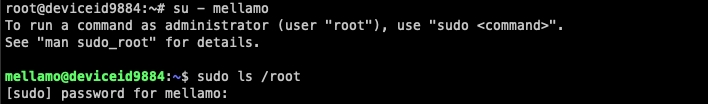 Testing sudo privileges
Testing sudo privileges
Disable Root Login
Disabling root login takes away an easy method for hackers to get in. The easiest way of accessing remote servers or VPSs is via SSH and to block root user login under it, you need to edit the /etc/ssh/sshd_config file.
From the remote server, open /etc/ssh/sshd_config
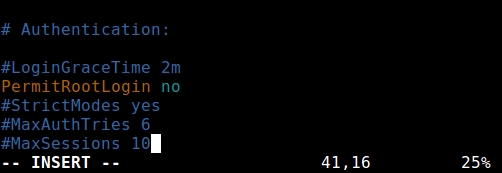 Set PermitRootLogin to “no”
Set PermitRootLogin to “no”
2. Save and exit sshd_config, then restart the service.
Copy SSH key
Return to you local machine.
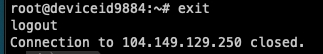 Log out of server
Log out of server
2. Copy your ssh key to the server
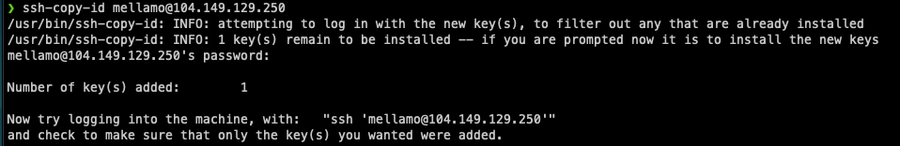 Copy keys
Copy keys
3. Confirm you can login with just your SSH key
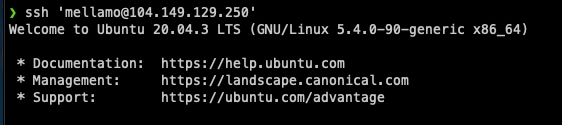 Log in with SSH key
Log in with SSH key
Done! You can now log in exclusively with your SSH key.
Disable Password Login
Now that you can log in with just your ssh key, you should now disable password login.
Return to your remote server, and open /etc/ssh/sshd_config again
2. Find ChallengeResponseAuthentication and set to no:
3. Next, find PasswordAuthentication set to no too:
4. Search for UsePAM and set to no, too:
5. Save and exit sshd_config, then restart the service.
Congratulations! You can only login with your ssh key now. Be sure to back it up in case something happens to your machine!
Last updated
Was this helpful?